It’s been drilled into our heads over the last decade: If you’re on the web and you’re handing over any personal information, make sure the site you’re using has HTTPS enabled. You’ll know the site you’re on is using HTTPS because it will have that comforting green-padlock symbol you see in every modern browser, a little visual cue that the site you’re using is secure. That green icon means the site I’m on is using something called Secure Sockets Layer, or SSL, (thus the S at the end of HTTPS).
For instance, if I head to PayPal in Chrome, even before I log in, I’ll see this:
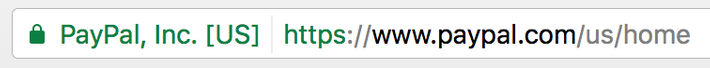
Thanks to efforts by Google, Facebook, the Internet Engineering Task Force, and others, nearly every site that will ask you for any sensitive data will use HTTPS. It’s been a vital step in creating a web that’s vastly more secure than what existed ten or 15 years ago. Sites using SSL certification allow for various types of encryption protocols, which greatly increase the difficulty of malicious users trying to do things like man-in-the-middle attacks, or spy on a connection while I’m logging into my bank account or webmail account — and a major part of that has been giving users that easy-to-understand, easy-to-see green icon.
For websites that want to offer HTTPS-secured browsing, they need to obtain an SSL security certificate, issued by an SSL-certificate-authority company. Until recently, website operators would need to pay a fee to get the certificate from companies like Symantec, Comodo, or Verisign. The certificate could be pricey, depending on how much traffic and secure connections you anticipated, and required a fair amount of technological savvy.
That changed with a company called Let’s Encrypt. Launched in 2016, the company removed fees for issuing SSL certificates, and greatly simplified the process of getting an SSL certificate. It’s, frankly, an admirable goal: Let’s Encrypt seeks to democratize SSL encryption for a vast number of sites that wouldn’t have been able to afford either the cost or the time to get an SSL through larger companies. It’s been wildly successful — it’s issued over 30 million SSL certificates to sites since it’s been founded.
But here’s the thing: Just because a site has an SSL certificate (and, thus, that little green padlock in your browser bar) doesn’t mean it’s a legit site, or that it’s actually the site it’s claiming to be. Vincent Lynch, senior security analyst for the SSL Store, thinks Let’s Encrypt’s mission to issue as many SSL certificates as possible has created a dangerous situation. Because Let’s Encrypt is easy and free to use, phishing and malware sites seem to have taken a liking to it.
Let’s Encrypt has issued, by Lynch’s count, 988 SSL certificates to sites with the word “PayPal” in them. Here’s a quick sample of just a few of the sites (all of which are now inactive) that had a Let’s Encrypt SSL certificate. All of these sites would have showed that comforting, little green padlock on the top of your screen if you had logged on, but judging purely by the URLs, you may have been in for a bad time if you had actually entered your PayPal username and password:
www.activity-paypal-account.tk
www.login-paypal-inc.com
www.paypal-co.com
www.paypal-verification-zone.com
www.verifyed-your-paypal-account.com
www-paypal-com-confirmation-limited.customers-area.tk
“Certificate authorities have traditionally said, ‘We’re not gonna give certification to potentially harmful sites,’” says Lynch. “Or ‘we’re gonna revoke the SSL certification so users can be aware.’” Let’s Encrypt, by its own admission, does not see moderating which sites get SSL certificates as part of its mission.
The sudden rise of PayPal phishing sites with SSL certification seems to have come around the same time as Let’s Encrypt. Before Let’s Encrypt began issuing SSL certificates, there were, per Lynch’s estimation, about 258 suspicious sites with “PayPal” somewhere in the URL. Now, there are nearly 1,000. (Lynch isn’t the only one to point this out; security researcher Eric Lawrence pointed out the same problem earlier this year.)
Lynch’s request to Let’s Encrypt is this: Stop issuing SSL certificates to any site with “PayPal” in the name, and thus remove that green-padlock icon from browser bars that may confuse less tech-savvy users (or just anyone who isn’t paying close attention to a URL).
But Josh Aas, executive director at Let’s Encrypt, says it’s just not that simple. “Do you think it would end at just blocking PayPal?” asks Aas. “There’s no way we stop at PayPal. It’s a slippery slope, and I think it’s a pretty disingenuous argument.”
For Aas, asking a company like his, which is attempting to spread SSL certification as broadly as possibly, would be impossible. “We simply don’t certify sites as safe,” says Aas. “That’s not what our certificates certify. Even if we wanted to, we’re not in a place to police content.” For Aas, it also starts to get into the concept of censorship — why should Let’s Encrypt start drawing lines in the sand about which sites are allowed to have SSL certification and that green padlock, and which are not?
(It should be noted that Lynch’s employer, the SSL Store, which resells SSL certificates from larger sites, is in some ways a competitor to Let’s Encrypt, though the two operate in very different arenas — Let’s Encrypt is largely a do-it-yourself operation, while the SSL Store offers a much more hands-on customer-service experience.)
Lynch agrees that Let’s Encrypt is well within its rights — he just disagrees with its perspective. “It’s not breaking any rules; it’s not an error or security lapse,” says Lynch. “But stone-cold numbers are backing that these SSL certificates are only being used and abused. Let’s Encrypt should dispense with all the arguments and fix this problem — a problem that is clear and quantifiable.”
Aas doesn’t see Let’s Encrypt, or any SSL-certification-authority company, as being the best place to fight against phishing and malware. For Aas, the real problem is that we’ve grown far too reliant on that safe, little green-padlock button: We see it, and we assume we’re safe from anything, instead of realizing that we’re just on a secure connection.
The problem of phishing sites using SSL certificates is a problem for companies that design browsers, like Google or Microsoft. “They have the resources to identify issues, and have more data on more users,” says Aas. “Microsoft can figure out if it’s a phishing site, and it can say, ‘Hey, this is a phishing site.’ That’s where this stuff needs to happen.”
I have a lot of sympathy for Aas’s point of view. Asking an organization like Let’s Encrypt to serve as gatekeeper for every website that wants to get SSL certification would be incredibly onerous, and would likely put an end to the good work it’s doing in making SSL certification even more of a standard on the web. And there’s something to the argument that once you ban a certain word, like “PayPal,” you’ve set a precedent to ban others.
On the other hand, phishing sites — particularly sites that would allow malicious users to gain access to sites like PayPal, which are likely linked to users’ bank accounts and credit cards — are incredibly harmful. After scanning through the 988 PayPal SSL certifications issued by Let’s Encrypt, Lynch’s judgement is blunt. “Just half a percent or less of these sites have a legitimate use. Everything else is just being used to harm the web.”
Google, Mozilla, Safari, and Microsoft all do a decent job of warning you against phishing and malware sites once they’re discovered, but those phishing and malware sites have to be discovered first. And with the ease of new sites gaining access to SSL certification, it’s possible that harmful sites still slip through your browser’s defenses before the URL is flagged — but still appear in your browser with that green padlock showing it as secure.
The vast majority of my life is now contained in digital files, whether it’s how much money I have in my bank account, my medical health records, or tens of thousands of personal and professional messages. This was a somewhat-concerning situation 20 years ago, when most of that information was on my local, crappy Gateway desktop, but now nearly all of that data sits in a cloud server somewhere — a server that requires just a username, a password, and perhaps a (easily bypassed) form of two-factor authorization. Creating a web that’s secure can no longer just rely on SSL certificates and checking for that green padlock; there will have to be a broad push toward better design, more consumer education, and perhaps the creation of some regulatory body that attempts to stamp out truly malicious sites targeting average web users — long before someone accidentally coughs up their PayPal password to www.paypal-bank.very-real-site.ru.
Until then, just because you see that green padlock at the top of your browser, don’t assume you’re completely safe.