Ransomware can be incredibly lucrative for cybercriminals. Older forms of fraud, such as the 419 Nigerian spam emails of the late ’90s and early aughts, required a large workforce to continue to string along the unwitting into sending actual money. Even breaking into the databases of large companies and swiping customers’ credit-card info is a bit of work — once a hacker has possession of the credit-card number, they need to sell them either to a middleman broker or directly to the black market. It’s a complicated ecosystem that requires management. You can still make money, but it takes a bit of effort to navigate an underground economy.
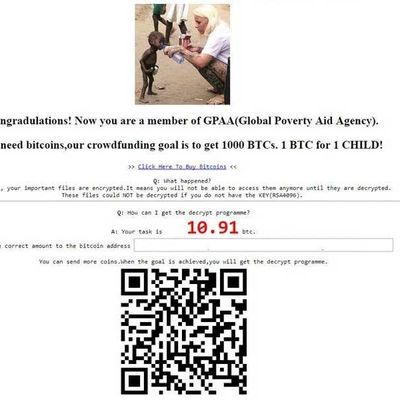
But a well-executed ransomware can quickly net you a fair amount for very little effort. And one particularly shameless form, spotted by Michael Gillespie and reported on by Bleeping Computer, is now making the rounds. Dubbed, for now, “GPAA,” it uses a stolen picture of Danish aid worker Anja Ringgren Lovén giving water to a Nigerian child (likely taken from her Facebook profile or from this International Business Times article) at the top of the ransom note.
The ransomware then claims, “Congradulations! [sic] Now you are a member of GPAA (Global Poverty Aid Agency).” Unsurprisingly, there is no such agency — doing a search for it only turns up reports of the GPAA ransomware.
Usually, ransomware is either threatening (e.g., “You have 48 hours to pay up, or the files disappear forever”) or slightly bemused (e.g., “Lol, looks like you got screwed up. Pay up and and we can make this go away”). GPAA plays on a slightly different set of emotions, claiming to be a charity organization that just happens to encrypt nearly every type of file on your computer. The amount demanded can vary wildly — Bleeping Computer shows a ransom note demanding 1.83 bitcoin (about $5,000 USD at current prices), while another found over at the Sensors Tech Forum shows a ransom of 10.91 bitcoin (or about $30,000 USD). Ostensibly, when the malware authors hit 1,000 BTC (or $2.7 million USD), they’ll release all the decryption codes to victims.
For those infected with the GPAA ransomware, there’s little they can do. The ransomware uses Cerber v6, a sophisticated and increasingly popular form of ransomware attack. It’s not currently possible to decrypt the files locked up by Cerber v6.
Your best line of defense? Keep your computer’s software up-to-date. Use an antivirus program, and keep that up-to-date as well. Don’t run random .exe files you aren’t 100 percent sure about, and never download a file from an unknown sender or click on a pop-up ad on the internet. Always, always, always back up your hard drive on a regular basis, and keep that backup unconnected from your computer when not in use. If worse comes to worse, you can just wipe your hard drive and start over.
Most experts warn against paying up unless your circumstances are truly dire. And even if you do pay off the ransomware authors, there’s never any guarantee that you’ll actually receive the decryption code.
Finally, if you actually want to help fight global poverty, donate money of your own accord. (This list is a great place to start.) Not only will you actually be helping people in need, but we’re pretty sure you can’t write off ransom paid via crypto-currency to hackers as charitable giving on your taxes.